Seirdy
Website and blog: https://seirdy.one/
Gemini: gemini://seirdy.one
Main fedi: @seirdy@pleroma.envs.net
Other contact info: see website
[Verifying my OpenPGP key: openpgp4fpr:AC6AF1F838DF3DCC2E47A6CF1E892DB2A5F84479]
- 7 Posts
- 22 Comments

 1·3 years ago
1·3 years agoUnfortunately, Gitea (the forge software that powers Codeberg) has major accessibility issues. It’s not usable from most assistive technologies (e.g. screen readers). GitLab isn’t much better.
Sourcehut is pretty much the only GitHub alternative with good accessibility I know of.
This is their privacy policy: https://h5hosting-dra.dbankcdn.com/cch5/petalsearch/global/agreement/privacy-statement.htm?language=en-us
It includes detailed fingerprinting metrics like mouse behavior and font information.
I should probably link it, thanks for the feedback.
I said that about Petal because readers likely hadn’t heard of it and didn’t have any expectations. l assume readers already knew Bing, Google, and Yandex were bad for privacy.
Not at all; there are tons of newish engines out there, the best of which are trying to carve out a niche for themselves in an area that Google and Bing ignore. I listed 44 English engines with their own indexes, along with some for other languages which I’m unfortunately unable to review because I don’t speak the langs required.
On these engines, you won’t get far if you use natural language queries or expect the engine to make inferences. Use broad terms and keywords instead. I recommend giving Mojeek, Marginalia, Teclis, Petal (bad privacy, but usable through Searx), Kagi, and Alexandria a try.

 33·3 years ago
33·3 years agoThe reality is more nuanced than this. Wrote up my thoughts on my blog: A layered approach to content blocking.
Strictly speaking about content filtering:
declarativeNetRequestis honestly a good thing for like 80% of websites. But there’s that 20% that’ll need privileged extensions. Content blocking should use a layered approach that lets users selectively enable a more privileged layer. Chromium will instead be axing the APIs required for that privileged layer; Firefox’s permission system is too coarse to support a layered approach.

 2·3 years ago
2·3 years agoIf you’re asking for an open-source option because you want to self-host…well, at that point, you’d already have a web server. Just sftp/rsync the files over into a subdir of your web root.

 0·3 years ago
0·3 years agoI compiled a list of search engines that use their own indexes for organic results: https://seirdy.one/2021/03/10/search-engines-with-own-indexes.html
I’ll probably post a big update to that article at some point that compares if/how some of the listed engines process structured data (RDFa, microdata, JSON-LD, microformats 1/2, open graph metadata, POSH).
I typically use a Searx/SearxNG instance that mixes Google, Bing, and Bing-derivatives (e.g. DDG) with other indexes: Petal, Mojeek, Gigablast, and Qwant (Qwant mixes its own results with Bing’s). Petal, Gigablast, and Mojeek have been quite helpful for discovering new content; however, I wouldn’t use Petal directly due to privacy concerns. Using it through a Searx proxy you trust more seems alright.
If I know a query will give me an instant answer I want to use, I’ll use DDG.
Yep. Foot is Wayland-only
I should add that Alacritty running with X11 compatibility isn’t quite as fast as running it on Wayland. Both Alacritty and Foot can utilize Wayland’s excellent frame timing/vsync support to prioritize rendering only when the display refreshes. Doing so reduces load (esp. in Alacritty’s case since it can offload most work to the GPU), which is sorely needed because proper font rendering is an intensive process to do in a latency-sensitive manner.
Advanced font fallback is one of the defining features of the Foot terminal, if you’re interested. You can even specify different fonts, which is useful for e.g. getting emojis to fit in one cell.
Check out the
removeparamandredirectdirectives in the static filter syntax docs.
GitHub is both (proprietary) software and a service. The main product is the service, and the software is just a means to that.
The service consists of SaaS and/or paid support. They sell at least one of these to the military and/or ICE.
If GitLab or Sourcehut did something similar, the same would apply even those are open-core and FLOSS, respectively.
Given the attack surface of addons, I’ve downsized my addon usage.
-
I’ve replaced HTTPS-Everywhere with the built-in HTTPS-first/only modes in FF and Chromium.
-
In FF, I use userContent.css instead of Stylus.
-
I use uBlock Origin’s url-rewriting filters in place of redirection addons.
-
In Chromium, you can choose to have an addon only be enabled on certain sites. I do this with Stylus and Dark Background Light Text.
EDIT: more information:
- I have a shell script that uses regex to “clean” urls in the clipboard and remove tracking params instead of the CleanURLs addon, since this is most useful when sharing links with others. I’ve gotten in the habit of previewing URL content before navigation (e.g. with a mouseover or by pasting into the URL bar) as well. If I want to navigate to a messy url, I just copy it and enter a keybind to clean the copied URL.
I use multiple browsers and profiles.
-
Normal browsers: Firefox with Cookie Autodelete, uBO, Stylus, Dark Background and Light Text; Chromium with uBO and Stylus. Stylus is only selective enabled.
-
For security-sensitive non-anonymous stuff, I run Chromium with flags to disable JIT and to disable JS by default, in a bubblewrap sandbox. This browser profile has no addons.
-
For peak anonymity (e.g. when using one of my anon alts), I run the Tor Browser in a Whonix VM. For quick anonymity I just use the regular Tor Browser Bundle in a bubblewrap sandbox. In an act of mercy towards my weak 2013 Haswell laptop’s battery, I no longer run Qubes. The Tor Browser should not ever be used with custom addons if you want anonymity.
Because the Tor browser should never run with addons and because I use a browser profile that has none, I don’t want addons to be a “crutch” that I depend on too much.
I do global hostname-blocking at the DNS level, so I can live without an adblocker. DNS blocking doesn’t do fine-grained subpage-blocking, conditional blocks, cosmetic filtering, redirects, etc. so a more complete solution is still worthwhile.
I also try to avoid injecting content into webpages with JS enabled, since that is extremely fingerprintable and opens a can of (in)security worms.
Some addons that I do not recommend at all:
-
Canvas Fingerprinting Defender: injects JS into pages, which is very fingerprintable and can trigger a CSP report if you don’t disable those. CSP reports can identify you even if you disable JS execution.
-
Anything that you can do without an addon, TBH. They do weaken the browser security model.
-
I agree that the PR process is bureaucratic, but that’s not the workflow that Git was made for. It’s a workflow popularized by GitHub.
The workflow that Git was made for was “make commits” + “export patches” + “send patches”. This typically happens over a mailing list. Under this workflow, sending a contribution is a two-step process:
git commitandgit send-email. The recipient could be a mailing list, or it could just be the developer’s email address you grabbed from a commit message. That’s part of the reason why Git has you include your email in every commit.

 2·4 years ago
2·4 years agoIRC diehard checking in. I prefer IRC to Matrix (been using both daily for a year or two now), but a switch wouldn’t be the end of the world.
Matrix has a high and growing complexity that makes developing a new client/server hard; as the spec grows, devs need to keep updating servers/clients with new features or risk being left behind. IRC clients can be whipped up by an individual in a short amount of time and then enter “maintenance mode”.
System requirements for running a Matrix server are extremely high with Synapse, and not that great with Dendrite and Conduit compared to most IRC implementations because of the need to sync room histories.
Matrix also has a lot of features that I’ve come to find unnecessary/distracting: typing notifications, stickers, profile pics, etc. It’s possible to carve out a subset of the protocol and just use that, but at that point it’s probably better to just use IRC.
mkdir ~/Documents/Notes cd ~/Documents/Notes $EDITOR name_of_note.txtFor lecture notes, I do this:
$EDITOR "$(date +'%Y-%m-%dT%H:%M:%S%:z').md"I don’t actually type out commands like these; I have alises for them. I sync my notes with
git, so I don’t have to learn another tool just for notes.
I updated the “What explicitly opting out actually entails” section to further elaborate on why adding this header might not really improve user privacy.
Server side categorization for sites with ads is where this Permissions action is aimed at. What this is saying is that if an ad tries to get a cohort id from an opted-out site, it will receive a meaningless default value. This knowledge is for the benefit of advertisers, not webmasters.
The solution is not to include trackers on your page in the first place, such as third-party ads. Permissions-Policy applies to the page requested and its contents.
As for cohort calculation, things are messy. If one site is opted out and another consequently has a greater weight, the implications wrt. fingerprinting are vague. Opting out doesn’t necessarily reduce a user’s fingerprint. FLOSS is one aspect of a user’s interests, but there are countless others. There is/was no legal or technical obligation to obey either the DNT header or this permissions-policy header (strictly for the purposes of cohort calculation), since the latter isn’t standard usage of the permissions-policy header and the former isn’t even a standard header in the first place.
A coordinated effort is better spent getting users off Chrome than getting upstream software and webmasters to add this band-aid to their sites.
I updated the article to explicitly address this; check the “What explicitly opting out actually entails” section.

 61·4 years ago
61·4 years agoI wrote about both issues, and why Matrix isn’t a perfect solution, previously: part 1, part 2. Starring WhatsApp, Firefox, Signal, XMPP, Email, and Matrix.
Also discussed on Lemmy: part 1, part 2.
Signal’s problem is being a closed platform; Matrix suffers primarily from complexity. Both enable dependence on a single small group, and therefore enable user domestication. That being said, Matrix is considerably less bad than Signal.
For large public rooms, IRC continues to be the best option. All its issues are client-side; IRCv3 supports history, multiple devices, authentication without NickServ, and even typing notifications. All these features are supported on Oragono. For small, private E2EE rooms, all existing solutions have major trade-offs.


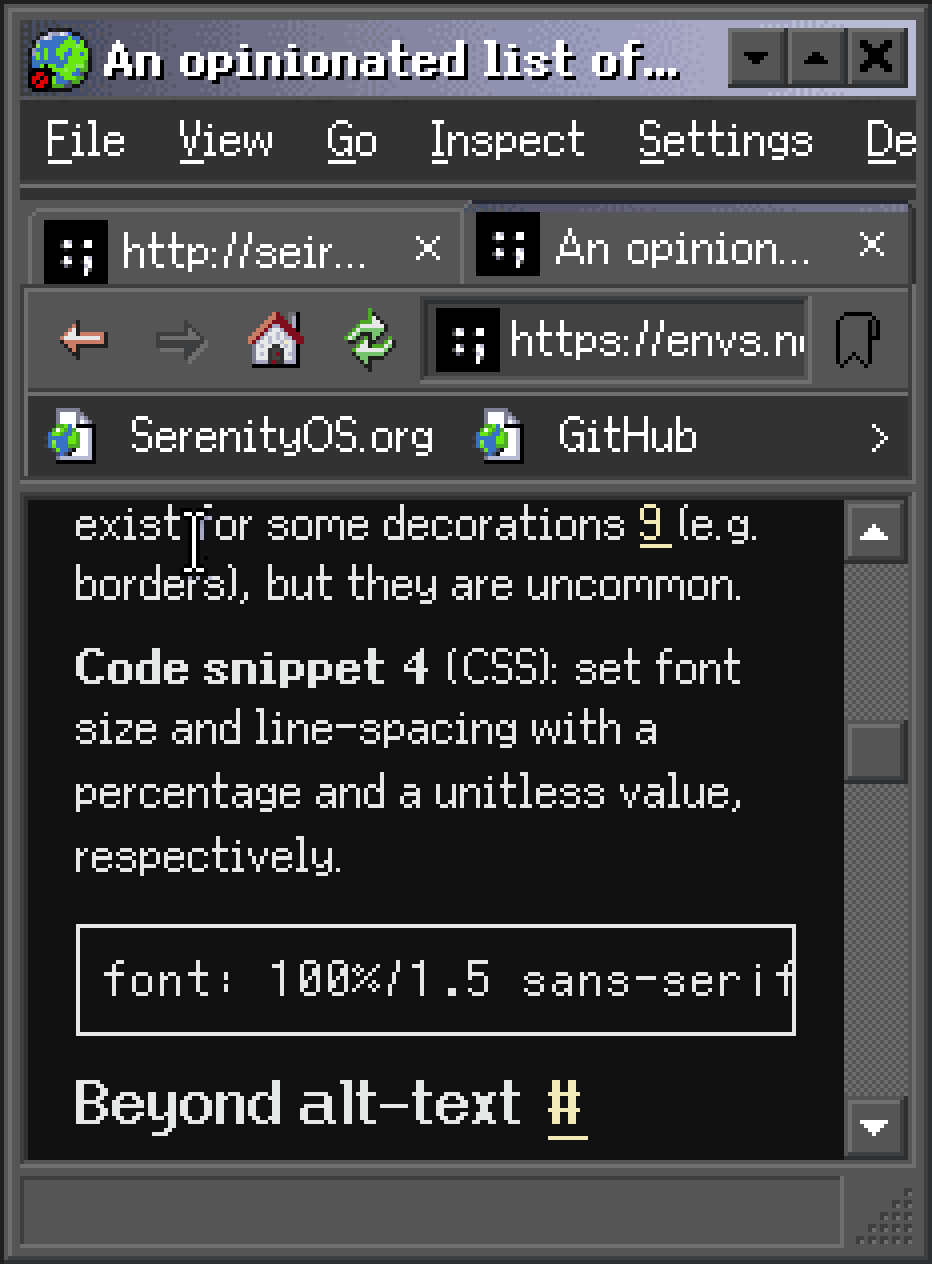
The good: familiar UI, nice community
The bad: much worse accessibility.
Conclusion: I’d recommend keeping a Gitea/Codeberg remote but not using it exclusively. Doing so should include more people without excluding people who use assistive technology.