I’m using Signal, but after I found out that it’s not as privacy-friendly as it claims, I’m uneasy about sharing my address there. I trust the person who asked for my address, but not the service. What’s a safe way to share? I was thinking of something like a self-destructing pastebin, but surely you have better ideas.
Which of Signals privacy claims are false?
Pretty much everything about it is unverifiable, because its a centralized service and you ultimately don’t know what the server is running. Contrast that with self-hostable apps which must pass verifiability checks, because people can host their own instance.
Clients are open source. Independent clients exists and they work. So the server must kind of do what signal claims, otherwise those devs would notice.
You have no idea what the server is running. It has your phone number, ie your real name and address, and it knows who you sent messages to.
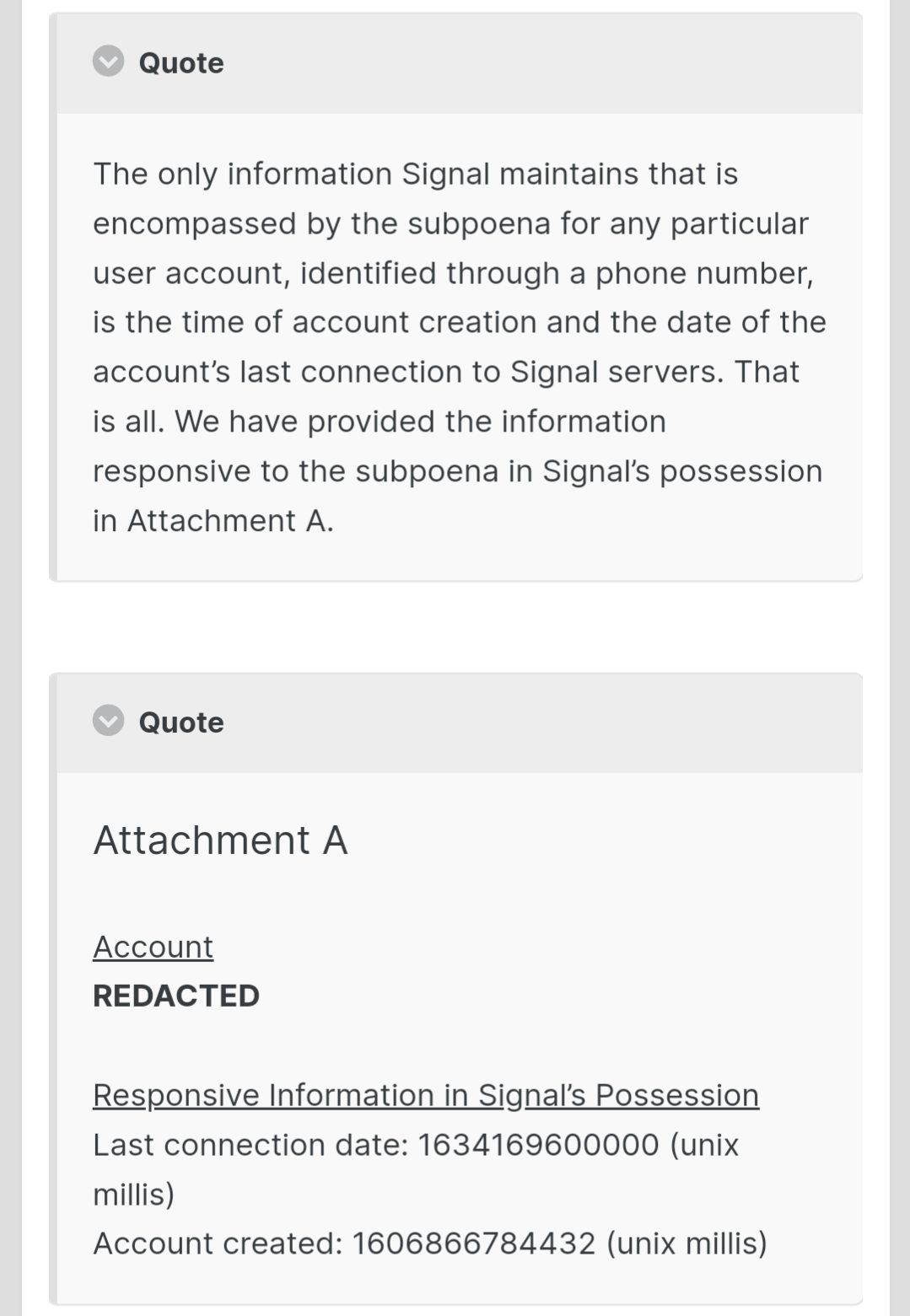
But it doesn’t though. That information has been subpoenaed from signal in the past. They don’t have access to it to give. This is public information.
As comment in thread points out, the subpoenaed info was essentially useless.
Yeah that’s exactly my point. Other guys was listing all these things the signal has stored but they really just don’t want access to any of it.
This is suspicion on the level of “you can’t be sure reality didn’t just pop into existence 10 seconds ago”. You can never be 100% sure of what others are doing on their hardware, or of anything really, especially if other people are involved. Your chat partners could leak all your chats and metadata for all you know!
What we do know is that Signal is operated by a non-profit foundation, their client and protocol are open source and considered the gold standard for privacy by pretty much every expert on the subject, they had multiple independent audits and a very good track record, they were subpoenaed and couldn’t comply because they didn’t have the requested data. That’s about as good as you can get.
deleted by creator
Better use a cipher then for your pen and paper transmission. Invisible ink as well.
Matrix and even Signal you reject for some reason work fine with no one being able to see the content of your message except the one you sent it to.
I’ve never heard anyone other than OP have any privacy concerns over Signal. Their encryption method is rock-solid, and they win the award for best response to a government subpoena
I have been using bw for years and never occurred to me to click on send. I thought it was for sharing passwords or something.
I mean it can be. You can put anything you want there and send it on it’s way
Signal is trustworthy
I guess you can use wormhole to transport the data to your peer, and if you’re extra paranoid encrypt it asymmetrically with something like age.
Then again you can just encrypt it with age and send it over Signal. There should be no risk involved in sharing public keys even if you don’t trust their servers.
Use briar.
Don’t use Briar.
Briar [0] gets funded by the OTF [1]. If you’re unfamiliar with the OTF, they’re publicly listed as a subsidiary of Radio Free Asia, a US state-run organization whose main goal (along with the other “Radio Free” incarnations such as Radio Free Europe, or Free Cuba Radio) is regime change for those Asian governments who don’t align with the US’s foreign policy interests.
The Radio Free agencies underwent a public re-branding in the early 1990s, but they are in effect the same CIA misinformation organizations from the 1950s:
Radio Free Asia began broadcasting to mainland China in 1951 from an elaborate set of transmitters in Manila. It was an arm of the Committee for Free Asia, and the C.I.A. thought of it as the beginning of an operation in the Far East that would rival Radio Free Europe and Radio Liberty.
It was only after Radio Free Asia’s transmitters were operating, according to sources familiar with the case, that the C.I.A. realized that there were almost no radio receivers in private hands in mainland China. An emergency plan was drawn up. Balloons, holding small radios tuned to Radio Free Asia’s frequency, were lofted toward the mainland from the island of Taiwan, where the Chinese Nationalists had fled after the Communist takeover of the mainland in 1949. The plan was abandoned when the balloons were blown back to Taiwan across the Formosa Strait.
What Allen Weinstein, one of the founders of the National Endowment for Democracy (NED), another US “human rights” regime change org said of his organization applies equally to the Open Technology fund: “A lot of what we do today was done covertly 25 years ago by the CIA.”
The fund is designated to: “support open technologies and communities that increase free expression, circumvent censorship, and obstruct repressive surveillance as a way to promote human rights and open societies.”
One should question the commitment of a fund that dedicates itself to “obstructing surveillance”, while being created by a government who runs the most expansive surveillance system in world history. And how the US might define the terms “human rights”, and “open society” differently from those who know the US’s history in those areas.
[1] https://www.opentech.fund/results/supported-projects/briar/
[2] https://dessalines.github.io/essays/why_not_signal.html#cia-funding
/s
Just a light jab, no harm intended.
All kidding aside, Briar is a great option, but so is Signal.
Signal enforces E2EE, is open source, has reproducible[3] builds (you can trust the app is what’s in public code), and best of all, because it is the gold standard of modern secure messaging apps, is under the scrutiny of many security experts. Finally, Signal has undergone various security audits [4] which they make public.
The reality of the situation is that if you’re a person of significant interest, someone with enough power can theoretically compromise you. The only way around it is to go completely open source hardware AND software, read every line of code, understand it, and compile everything yourself.
I will say, while I’m a Staunch supporter of Signal, Briar is what I’m keeping my eyes on for the future. It still needs to reach feature parity with most modern apps, and make it stupid easy to connect with people who are already in your contacts (I’m not going to ask my grandma to install Briar), but the tech behind it is pretty great [5] and only getting better.
[3] Only for Android.
[4] https://community.signalusers.org/t/wiki-overview-of-third-party-security-audits/13243
[5]
Yes, we should absolutely put extra scrutiny on radio free asia funded projects. But is briar a single, centralized US hosted service? Does it require you, like signal, to give it info that links to your real identity? Did it close its server source code off for a year? Is it possible to download it from f-droid so you can verify its builds are secure? Does it depend on google or amazon? Does it bundle in a cryptocurrency? Is it possible to verify what the server is running?
OTF is no longer run by Radio Free Asia
But is briar a single, centralized US hosted service?
No. But Briar runs over the Tor network, another project funded by the OTF [0]. Side note, the Tor Project has received $3 million USD from the OTF/CIA, can you trust it when a researcher was able to identify Tor users 100% of the time in a lab experiment and 81% of the time in real-world tests [1][2]?
Does it require you, like signal, to give it info that links to your real identity
Signal never touted anonymity, only privacy. You need to understand your threat model to make an informed decision. Also, if a single researcher was able to de-anonymize Tor users 80% of the time in real life, what chance do you have with a more powerful nation-state, unlimited funds, and ownership of various exit nodes?
Did it close its server source code off for a year?
“Never attribute to malice that which is adequately explained by stupidity” - in this case, we can replace stupidity with a million things that have nothing to do with compromising your privacy, the client is still completely E2EE, open source and has reproducible builds.
Is it possible to download it from f-droid so you can verify its builds are secure
You can download the app directly from Signal [3] or even build it yourself [4] to verify the build in the play store matches the code on github
Does it depend on google or amazon?
If you’re using an Android phone, you’re likely already depending on Google, although you can still run it on a de-google’d phone. I’m using Signal on a Pixel with stock Android and a OnePlus without any ties to Google using LineageOS, it works great on both phones! It does run on Amazon infrastructure, but again, we’ve seen Tor is not guaranteeing anyone anonymity anyways.
Does it bundle in a cryptocurrency?
How is this a negative? Some people want this and if you don’t want it, don’t use it.
Is it possible to verify what the server is running?
The server is basically plumbing/a router. The bulk of the Signal “magic” happens in the E2EE app. Can you verify that your Briar messages aren’t hopping through government run Tor bridges/relays/exit nodes?
[0] https://www.opentech.fund/results/supported-projects/tor-project/
[1] https://www.vice.com/en/article/4x3qnj/how-the-nsa-or-anyone-else-can-crack-tors-anonymity
[2] PDF warning: https://mice.cs.columbia.edu/getTechreport.php?techreportID=1545&format=pdf
can you trust it when a researcher was able to identify Tor users 100% of the time in a lab experiment and 81% of the time in real-world tests [1][2]?
I know that you are doing this conspiracy thinking on purpose to confront Dessalines about their bias, but while this is not obvious to everyone:
While it is true what you say, it is beyond meaning for the most usage of Briar. The researchers result depended on a honeypot that served a large file. Don’t have contacts that act as honeypot and you’re safe. When chatting with strangers, the technique discovered by that researcher might not be relevant to Briar, but I have not enough knowledge to make a claim about that.
Never knew this before I didn’t know they were funded by Radio Free Asia
@KLISHDFSDF You may like to make a TL;DR that clarifies the intention of that post.
It’s very confusing for anyone who didn’t read Dessalines anti signal article, and even more if one doesn’t know that you are questioning their conspiracy thinking.
Anyway, don’t use Signal, Briar and Tor, they are shit-lib-CIA regime change tools. [meta: the last sentence is sarcastic]
You could make a quick phone call, I mean Signal requires a phone number, might as well make use of it!
PrivateBin is pretty solid and maintained https://github.com/PrivateBin/PrivateBin
I was reading about privatebin, is not perfect but is the best paste bin that I seen.
Jami is anonymous when it comes to account creation, and p2p, so the accounts are only created on-device, and disappear from existence completely when all connected clients are deleted. It’s also end-to-end-encrypted.
A third party could find out your IP address if they monitored your network traffic, but not the content of your messages, and not that you are messaging someone. Only that you are using the p2p protocol for something.
Imho the doubts about signal are legitimate but way too overblown. Signal has sealed sender, so nobody could (easily) know who sent the message, a VERY strong cryptographic protocol and encrypted profile information. Sure, it’s centralized and it collects your phone number when you sign up, but your messages are safe, they are not stored in the cloud and even if they were collected, all the information would be useless thanks to the signal protocol. I understand that the doubts are in good faith but they dismiss every effort made to bring a solid, private messaging app like signal to the general public. You can’t self-host, third-party clients are not officially supported and the service it’s centralized, but that’s a matter of freedom, not privacy. If it makes you feel better you can use matrix, but the problem you’re trying to solve doesn’t exist
deleted by creator
Op you can do this it’s 1 xtra step for you and another xtra step for your reciever but it has less commitment than finding and changing to a whole different app.
You can also check out Onionshare
Self-destructing pastebin could be less private than Signal, as they’re not encrypted on the server side. If you both know how to encrypt and decrypt, you can encrypt a text file yourself and send it. Otherwise, you’d have to end up trusting one service or another.
https://1ty.me would be described as a “self-destruting pastebin.” I’d generally be careful about what you can put in there (e.g. put partial information in it with no context) but it seems to do the job.
But the real answer is probably PGP/GPG.
Here is a good resource for these kinds of questions: https://www.privacyguides.org/en/tools/













